You can automatic enable Bitlocker on your Hyper-V Gen 2 virtual machine during OSD, please read Niall Brady’s post Here
But if you already install a Hyper-V Gen 2 virtual machine, and you want to enable bitlocker, you can do it manually. Here are the steps:
- Open cmd as administrator
- Set XTS-AES256 Engryption
REG.exe add "HKLM\Software\Policies\Microsoft\FVE" /v "EncryptionMethod" /t REG_DWORD /d 7
- Allow enable bitlocker for no TPM chip
REG.exe ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /v UseAdvancedStartup /t REG_DWORD /d 00000001 /f REG.exe ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /v EnableBDEWithNoTPM /t REG_DWORD /d 00000001 /f REG.exe ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /v UseTPM /t REG_DWORD /d 00000002 /f REG.exe ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /v UseTPMPIN /t REG_DWORD /d 00000002 /f REG.exe ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /v UseTPMKEY /t REG_DWORD /d 00000002 /f REG.exe ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE" /v UseTPMKeyPIN /t REG_DWORD /d 00000002 /f
- Add recoverypassword
manage-bde.exe -protectors -add C: -recoverypassword
- Enable bitlocker with password
manage-bde -on C: -pw
- Create a password, you won’t see anything when you type it.
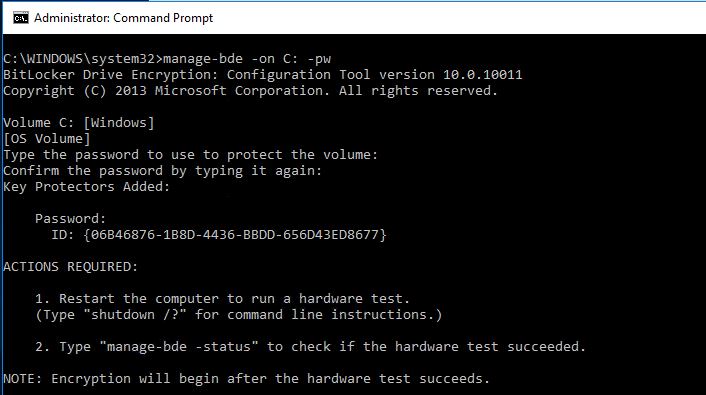
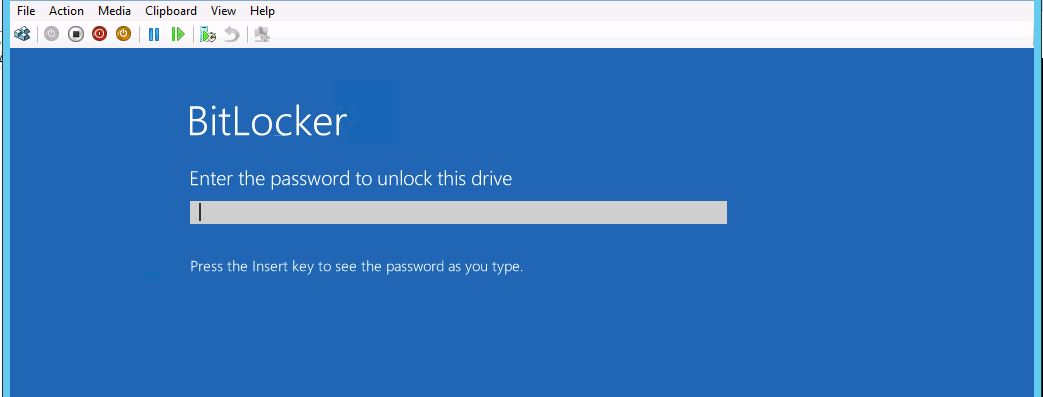
- Restart virtual machine, it will ask for your bitlocker password
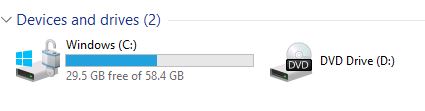
- Check if you C drive has bitlocker enabled.
What about OSManagedAuthLevel parameter stored at HKEY_LOCAL_MACHINE SOFTWARE Policies Microsoft TPM? Should I set to 4?
Hello, I think it’s not necessary use that registry for this scenario. I should have updated this blog post as well, using these registry from this old post is only for if your virtual machine doesn’t support TPM. If your host Hyper-V server is Windows 10 or Server 2016/2019, that will support virtual TPM for virtual machines, and you won’t need to do what is mentioned in this post. It’s better use GPO, or ConfigMgr MBAM or Intune to manage bitlocker settings.
Thank you!