Has been long time writing a blog post in here, not quite sure what topic I was going to write. In past few days I was testing “Account Control”, I am not sure if this is an official wording, I just can’t figured out better words for it. I wanted to know more about the Settings–Accounts page, how can I control it and what are the impacts. This is just my test notes sharing with you.
Microsoft Account Sign-In Assistant
I DON’T recommend disable Microsoft Account Sign-In Assistant. I quote this from Microsoft Doc https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-accounts#accounts-allowmicrosoftaccountsigninassistant
- If the MSA service is disabled, Windows Update will no longer offer feature updates to devices running Windows 10 1709 or higher
- If the MSA service is disabled, the Subscription Activation feature will not work properly and your users will not be able to “step-up” from Windows 10 Pro to Windows 10 Enterprise, because the MSA ticket for license authentication cannot be generated. The machine will remain on Windows 10 Pro and no error will be displayed in the Activation Settings app
What else? Disabling Microsoft Account Sign-in Assistant will also break your Autopilot white glove deployment. After white glove deployment succeed, policy profiles are applied (MSA Assistant is disabled), you will see the nice green screen that everything is fine, and you can reseal the device. But when user happily turn on the device, they won’t see the “Welcome to your organization” sign in page, instead it will be a normal consumer sign-in screen and asking NEW user. One of my friend run into this problem just few months ago.
If you blocked Microsoft Account Sign-in Assistant, this error will show up when you try add Microsoft account or Work or School account.
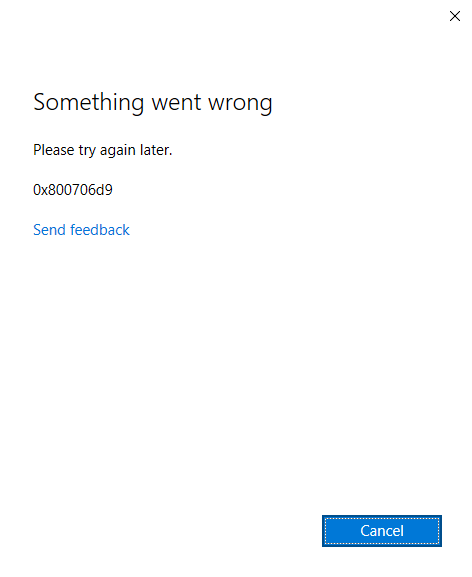
Forbid Microsoft Account
I am not saying you should forbid Microsoft Account or you shouldn’t for enterprise managed devices. As in-house IT or managed service provider, you may not want your user add their MS account to company devices, or Kiosk devices. But sure as an end user myself … *cough* *cough* 🙂
– Where is the setting?
In Intune, you can easily find this/these settings in Device restrictions – Cloud and Storage or use Intune Policy CSP https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-accounts

You will find the same settings in GPO: Computer Configuration\Administrative Templates\Windows Components\Microsoft account >>”Block all consumer Microsoft account user authentication” : Enabled. But please don’t get confuse with Accounts: Block Microsoft accounts , these are not same settings. More details about these two policy settings can be found in Microsoft doc https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/microsoft-accounts#block-all-consumer-microsoft-account-user-authentication
– What happens when forbid Microsoft Account?
Last year when Maurice and I were doing Kiosk device presentation in MMS Jazz conference, we mentioned Microsoft Account cause issues to Kiosk device, D.C Tardy from Microsoft was kindly enough gave us more details of this topic and allow us share their work. Thanks a lot!
What the CSP (and GPO equivalent) does:
- forbids applications using the web account manager (WAM) to authenticate using Microsoft account (MSA)
What the CSP (and GPO equivalent) does not perform:
- forbids applications using Oauth to authenticate using MSA
- forbids browser login (edge, chrome, application using browser authentication)
- disables the “Microsoft Account Sign-In Assistant” (wlidsvc) NT service
Why it may work for you:
- The applications you may be concerned about are the ones in Windows 10. The three we tested (mail, myphone, stickyNotes) are all using WAM. Additionally, Office (16.0.7967+), post Windows 1803 (RS4), uses WAM.
- Additional applications could be controlled by AppLocker reducing risk by blocking unapproved applications
- You may have a proxy server that includes data leakage protection (DLP) controls without the need to block login.live.com
What we tested using the CSP and found to work:
- Autopilot
- Windows update
- Office update
Additional caveats:
- Minimum Office version implementing WAM and so honoring the CSP is 16.0.7967 with Win10 1803
- There is a risk that the using this CSP may disable a feature you depend on now or in the future.
– What about Microsoft Store?
Microsoft Store is built in Windows app, you cannot remove it. We can download apps, games, tools from Microsoft Store. And what else? Language feature. So what happens when you blocks Microsoft Store? Here is a good example:
When Microsoft Store is not blocked
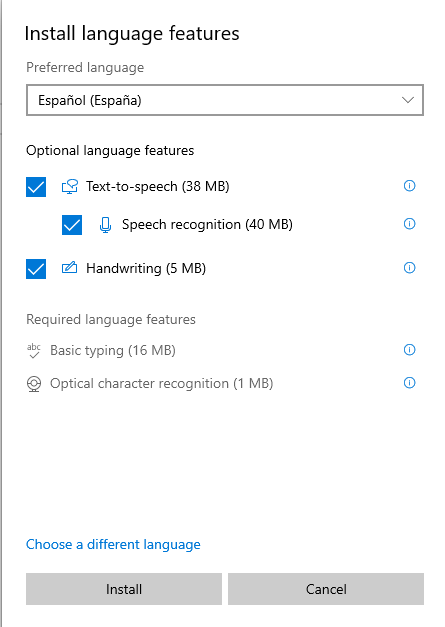
When Microsoft Store is blocked

Now you see the difference? Blocking Microsoft Store will also blocking Windows 10 install/update it’s language feature packages.
So how does this related to “Account Control”? This is totally depends on your management plan and your recourses. For resourceful and highly managed enterprise customers, I don’t recommend allow private store. Windows Store for business is managed way to deploy apps. I know there is rumors about Microsoft will retire Windows Store for business, but until any official statements comes out, I will still recommend use Windows Store business with company credentials.
If there is some reason need to allow users install apps from Microsoft Store by themselves, users don’t necessarily need Microsoft Account for this matter , please don’t register Microsoft Account just for install apps from Microsoft Store in company devices. There are two settings to help this, or actually just one: Computer Configuration\Administrative Templates\Windows Components\App Runtime >> “Allow Microsoft accounts to be optional” : Enabled. When user tries install something from Microsoft Store, they will see this notification, it doesn’t enforce you to logon Microsoft Account since user should be already logged on with company managed credential. Chose No, thanks will start download the app.

If you have configured Block all consumer Microsoft account user authentication as I mentioned earlier, when user choose Sign in , they will this function is blocked by group policy, which I think it gives enough message to users that they shouldn’t use their personal account in company device.
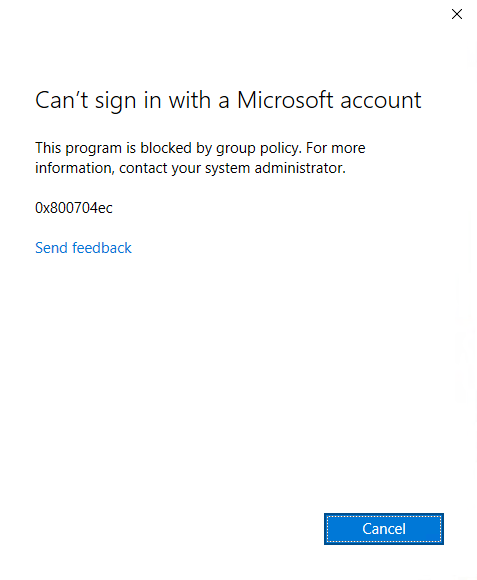
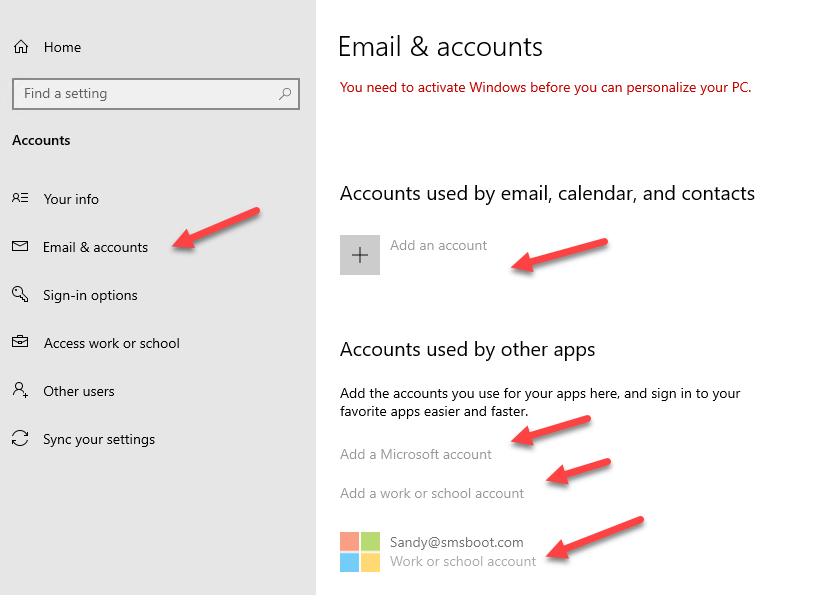
And this same above notification will show up when try use Settings\Accounts\Email & accounts >> Add a Microsoft account
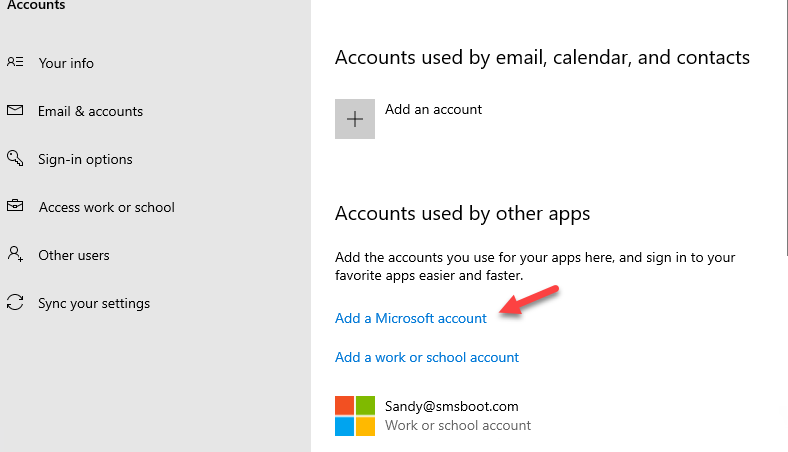
Greyed out Email & accounts
By using this registry HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Settings: “AllowYourAccount“=dword:00000000 , you can disable Settings\Accounts\Email & accounts page. Or use Intune Policy CSP https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-settings
This doesn’t forbid users adding Microsoft account nor work/school account via Office 365 apps , instead this just forbid deleted those accounts from this page.
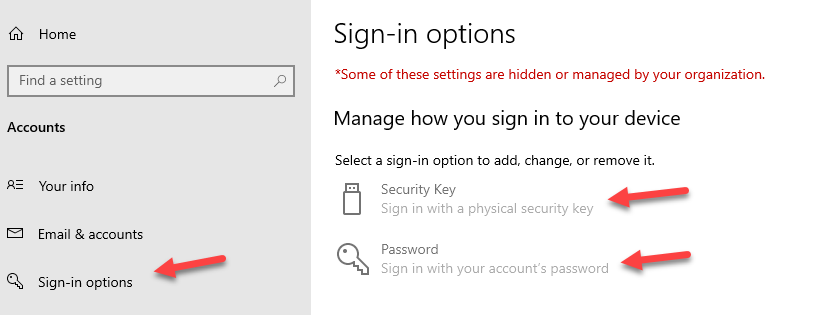
Greyed out Sign-in options
Use registry HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Settings: “AllowSignInOptions”= dword:00000000 can disable Settings\Accounts\Sign-in options page, or use Intune Policy CSP https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-settings
Even we can disable this page, I will still suggest use GPO or Intune Policy configure Sign-in options.
GPO: Computer Configuration\Administrative Templates\System\Logon
Intune: https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-credentialproviders
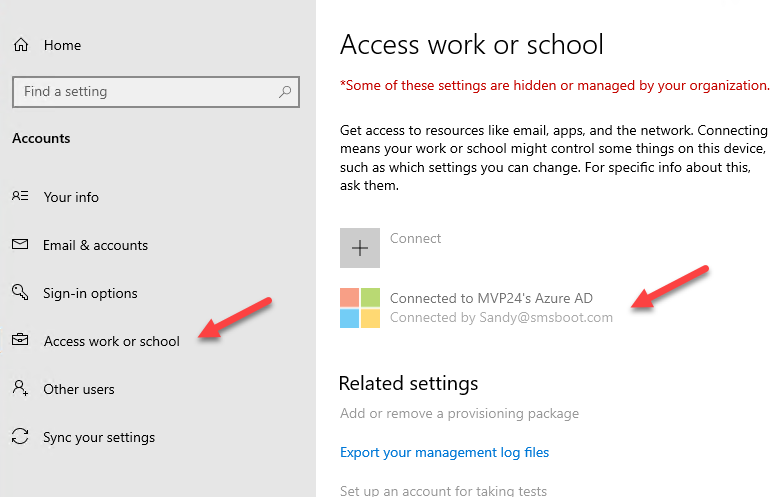
Greyed out Access work or school
Use registry HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Settings: “AllowWorkplace“= dword:00000000 can disable Settings\Accounts\Access work or school page. Or use Intune Policy CSP https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-settings
In some case you might want to use this. For example if user has local administrator rights, and you don’t want user disconnect the device from their work account. Sure you will still need other restrictions as well, like use Applocker restrict access to PowerShell.exe, cmd.exe and so on.
This setting doesn’t forbid adding another work or school account from Office 365 apps.
How can I block users from adding additional work accounts (Azure AD registered) on my corporate Windows 10 devices?
You can find the answers from Microsoft documentation https://docs.microsoft.com/en-us/azure/active-directory/devices/faq#q-how-can-i-block-users-from-adding-additional-work-accounts-azure-ad-registered-on-my-corporate-windows-10-devices
A: Enable the following registry to block your users from adding additional work accounts to your corporate domain joined, Azure AD joined, or hybrid Azure AD joined Windows 10 devices. This policy can also be used to block domain joined machines from inadvertently getting Azure AD registered with the same user account.
HKLM\SOFTWARE\Policies\Microsoft\Windows\WorkplaceJoin, “BlockAADWorkplaceJoin”=dword:00000001
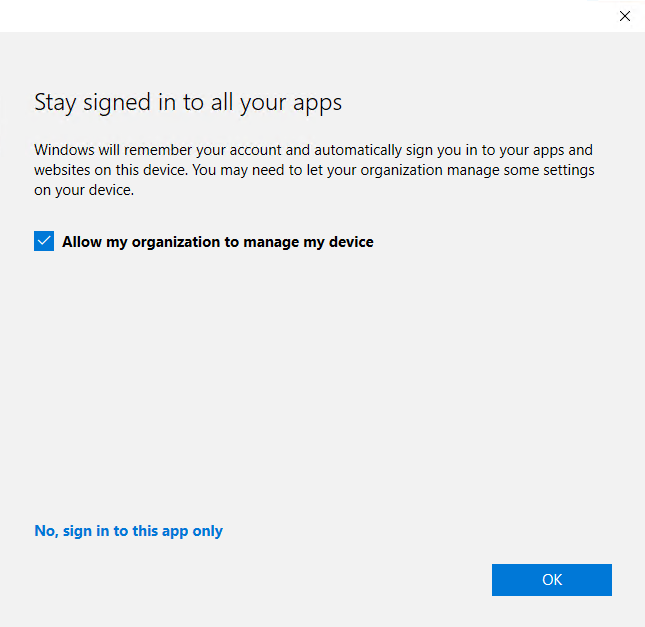
When a device is Azure AD joined or Hybrid Azure AD joined in one tenant, if user has multiple work or school accounts, they can still do Azure AD register to another tenant, if they checked “Allow my organization to manage my device“, and choose OK.
When use this registry, your users will no longer seeing this notification again when they login Office 365 apps with another work or school account, device will not be registered to another Azure AD tenant (Azure AD register), but this also means there is no Single Sign On feature for those additional accounts, and it might still have other unexpected impact that I don’t know about yet.
There is extra information about this registry and Hybrid Azure AD join planning, details can be found in https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-plan#handling-devices-with-azure-ad-registered-state
About the above notification, I personally don’t like it much. There are four options here for users to choose:
- Click OK. Since it’s blue button, we easily click on it without much of reading or thinking. This will register your device to Azure AD, and remember user credential in the device for other apps
- Uncheck the “Allow my organization to manage my device, then click OK. This will not register you device to Azure AD, but it will remember user credential in the device for other apps
- Choose “No, sign in to this app only”. This will not register you device to Azure AD, and it only remember your credential for this app
- Close the window by click on X. This will just close the notification, doesn’t do anything else
We can always make a pretty instruction for our users, let them know which option they should use. Are we always make the right choice?
Summary
“Account Control” are very important, please test more before you configure any of them. I might still missing some information, let me know if there is anything else.

Good information, thanks for sharing this Sandy
Thank you!!1