Few weeks ago I decided to clean up my tenant, I noticed that I have lots of Azure AD service principals that are no longer needed, this is my oldest tenant and I have been testing for many stuff over past few years. My first plan was delete those what I have created, but there are lots of them. So I was thinking “how about I just delete all?“
There are some service principals are for internal usage in Azure, example “Microsoft Graph”, we can’t delete those from Azure Portal nor by PowerShell, which means it should be very safe run this one liner PowerShell to delete service principals (Don’t do that!):
Get-AzureADServicePrincipal | ForEach-Object {Remove-AzureADServicePrincipal -ObjectId $_.ObjectId}
Azure Tenant Default service principals
When we create a new Azure Tenant, these 16 service principals are automatically created. The highlighted three service principals “Microsoft password reset service“, “O365 Demeter” and “Azure Portal” can be removed by PowerShell, rest of those are internet service principals, removal is not allowed.
| DisplayName | AppID |
|---|---|
| Azure ESTS Service | 00000001-0000-0000-c000-000000000000 |
| Windows Azure Active Directory | 00000002-0000-0000-c000-000000000000 |
| Microsoft Graph | 00000003-0000-0000-c000-000000000000 |
| Microsoft App Access Panel | 0000000c-0000-0000-c000-000000000000 |
| Microsoft Graph Change Tracking | 0bf30f3b-4a52-48df-9a82-234910c4a086 |
| AzureSupportCenter | 37182072-3c9c-4f6a-a4b3-b3f91cacffce |
| Windows Azure Service Management API | 797f4846-ba00-4fd7-ba43-dac1f8f63013 |
| Microsoft.SMIT | 8fca0a66-c008-4564-a876-ab3ae0fd5cff |
| IAM Supportability | a57aca87-cbc0-4f3c-8b9e-dc095fdc8978 |
| Office 365 Configure | aa9ecb1e-fd53-4aaa-a8fe-7a54de2c1334 |
| Signup | b4bddae8-ab25-483e-8670-df09b9f1d0ea |
| AAD Request Verification Service – PROD | c728155f-7b2a-4502-a08b-b8af9b269319 |
| MCAPI Authorization Prod | d73f4b35-55c9-48c7-8b10-651f6f2acb2e |
| 93625bc8-bfe2-437a-97e0-3d0060024faa | |
| O365 Demeter | 982bda36-4632-4165-a46a-9863b1bbcf7d |
| Azure Portal | c44b4083-3bb0-49c1-b47d-974e53cbdf3c |
How about “Microsoft Intune”
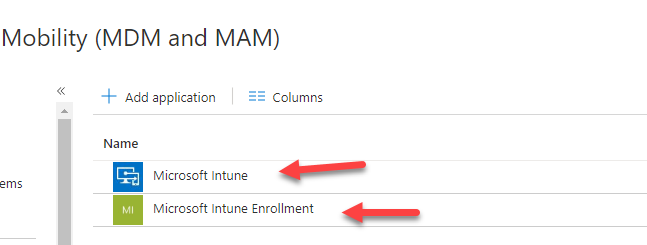
There is no Microsoft Intune service principal when create a new tenant without EMS or Intune licenses, this service principal is automatically created when we first time active EMS or Intune licenses, we can find this two application in MDM and MAM settings and from Enterprise Applications
What happened when delete Microsoft Intune service principal? Good question! I have tried it twice in two of my test tenants, so that I can confirm my results. After remove this service principal, I lost access to Intune blade, it behaved just like if I don’t have EMS or Intune license
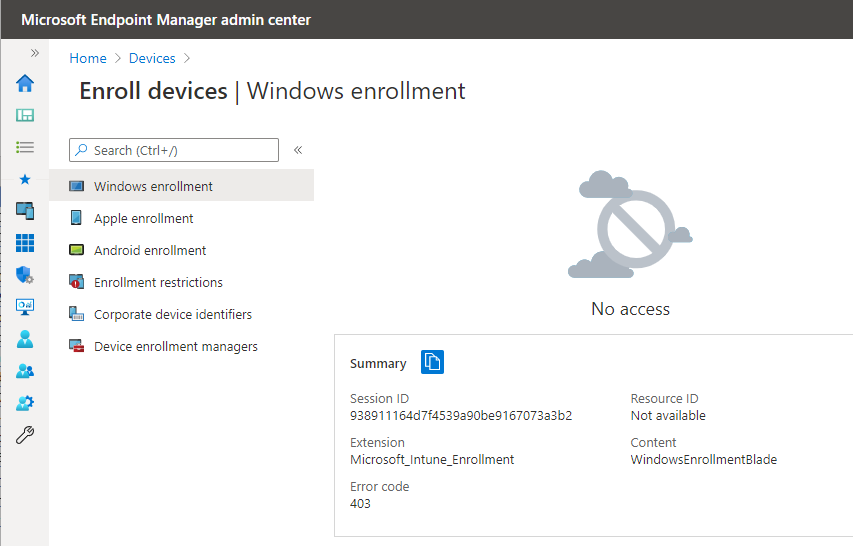
So can we fix this by create the Microsoft Intune service principal using PowerShell?
New-AzureADServicePrincipal -AppId 0000000a-0000-0000-c000-000000000000
Bad news! Even though I recreated this Microsoft Intune service principal, and my licenses are assigned, I still don’t have access to Intune. I have tried deleted all my license subscriptions, bought new license, and let the new license recreate this service principal for me, but still no luck.
So what now? In this moment when I am writing this blog, I have support case opened with Microsoft for over three weeks, support engineer has been advise me create new service principal, active MDM authority from office portal, none of theses helped. They have now promised they will try reproduce this issue and discuss internally what is the next step. I will update this post if I gets any results.
What do I learn?
- When create Azure Application, always assign owner, so that we know who owns this application, and no one delete your apps
- Any Global Administrator, Application Administrator and Cloud Application Administrator can delete applications and service principals, so make sure they don’t accidently delete “Microsoft Intune”
- Don’t delete anything that are allowed to delete
- Don’t do it
- Don’t do it
- Don’t do it
Good sharing! Very curious to know how did you fix this issue.
Microsoft Support fixed my issue. Also, I have heard from another friend of mine that Microsoft has improved this, the issue will be automatically remediated and fixed.